Compliance

The Business Email Compromise Handbook
A Six-Step Plan for Stopping Payment Redirection, Supplier Invoicing Fraud and Gift Card Scams Sometimes,...

Unlocking Collaboration: Making Software Work Better Together
The recent and rapid pace of change in the workplace has required companies to rethink their tools and...

Public Sector Cloud Journey
As the government continues to move workloads to the cloud, many agencies are struggling to automate...

An Overview of Insider Threat Management
As organistions move towards a more distributed workforce, the traditional perimeter of the office network...

The PMO that delivers
A modern PMO is no longer project focused, it is business focused. Instead of trying to ensure projects...

How Cloud Enables Modern Management For Midsize Firms
As midsize firms turn to cloud to enable the agility needed to compete in the future of work, most will...

7 Habits of Highly Effective DevSecOps Teams
Security teams are responsible for safeguarding assets in the cloud to maintain compliance and eliminate...

Engaging Workers, Growing Business, Protecting the Planet
Recent years have seen the world of EHS and ESG evolving rapidly. The time health and safety or environmental...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...

The Enterprise Guide to Multi-Cloud
Organizations of all industries and sizes are increasing cloud adoption to meet the demands of today...

CSI Endpoint Security Survey 2022
The unprecedented shift to remote work has changed everything. New data reveals what security professionals...
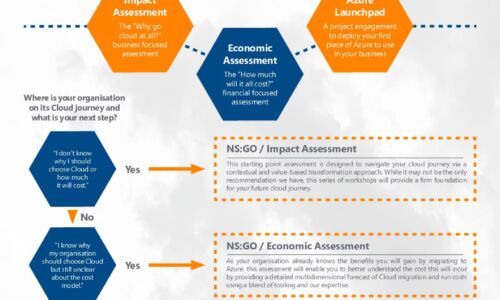
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

