Network

Unmasking BEC and EAC
Whether they result in fraudulent wire transfers, misdirected payments, diverted payrolls, supply-chain...

Accelerate Enterprise Cloud Transformation
Accelerate Enterprise Cloud Transformation Staying competitive in today's rapidly changing marketplace...

Unlock the Value of your Data with Simplified Database Management
If your organization is like most enterprises, your high-performance databases are supported by traditional...

Cybercrime tactics and techniques
2019 is off to an action-packed start in cybercrime. From a steadfast increase of pervasive Trojans to...
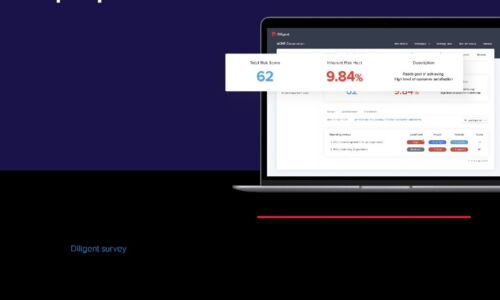
Effective CISO Presentations to the Board: Top Tips & Checklist
As a CISO, you have crucial info to convey about cyber risk, and your board wants to hear it. In a recent...

Three Ways to Make Cloud Your Business
The role of IT infrastructure and operations leaders has dramatically changed, and cloud evolution continues...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...

Ransomware Protection Checklist
Ransomware attackers are increasingly employing more sophisticated attacks and defeating existing defenses....

GigaOm Radar for Phishing Prevention and Detection
Get your complimentary copy of this independent GigaOm Research report, which analyzes positioning and...

Managing Mainframe Phishing Vulnerabilities
Mainframes are undisputedly the most mature, secure and best defended computing platform. Yet even mainframes...

Securing web applications in healthcare
You might think that healthcare would not be a target for criminals, but WannaCry – a strain of ransomware...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


