Hardware
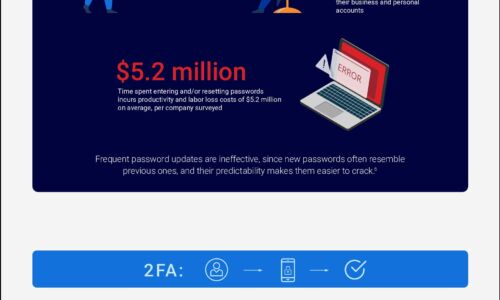
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Your Data. Their Cloud.
In today's organizations, digital transformation is a vital imperative—and cloud services offer a proven...

A CIO's Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

6 Steps to Implementing a Zero Trust Model
An all or nothing approach to Zero Trust is a tall task. What if you took a more incremental, agile approach...

Achieving pervasive security above, within and below the OS
It seems that every few months, another prominent global brand experiences a major security breach and...

Empowering Medical Manufacturers to Become Leaders
Due to increasing technology and product complexity, regulatory requirements and supply chain issues,...

The Definitive Guide to Migrating to the Cloud
To lay the foundation for modern application development, increase agility, and reduce cost, IT leaders...

Future-proofing endpoint management
New devices, platforms, applications, and technologies connecting to the network are overwhelming IT's...

Securing DNS by Design
3 Critical Protections from Your DNS Service: How Your Service Provider Can Protect Your Enterprise DNS...

The Pitfalls of SASE Vendor Selection: Features vs. Strategic Outcomes
After speaking with 1000s of IT pros, we've learned that success with SASE is only achieved when it meets...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



