ERP
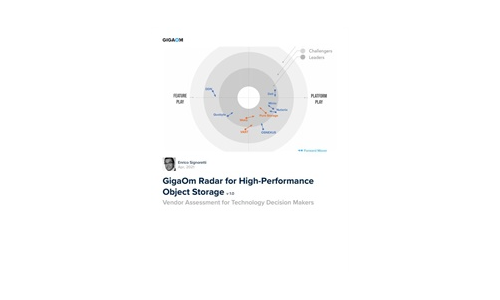
GigaOm Radar for High-Performance Object Storage
For quite some time, users have been asking for object storage solutions with better performance characteristics....

Assess Your Endpoint Security: MITRE Engenuity ATTandCK Evaluations
Making a decision on endpoint security tools is complex, so access to objective vendor-neutral information...

The Perimeter's Gone. Can Your Security Handle It?
Organizations need to shift their security strategy to secure the new ways work gets done. That takes...

Five Steps to Implementing a Risk-Based Due Diligence Program
Greater enforcement of Anti-Bribery and Anti- Corruption (ABAC) laws around the world have increased...

What you need to know about upcoming ESG regulations
New ESG regulations are being proposed across the world. But ESG is about more than just meeting requirements....

IT Infrastructure Made to Meet Modern Business Needs
IT modernisation is a key focus for many organisations. Legacy infrastructure and deep-seated operating...

CIO Roadmap to Hybrid and Multi-Cloud
While cloud has become a key driver of business expansion and operational efficiency, business and IT...

Forrester Consulting Study: Trusting Zero Trust
The growth of ransomware and work-from-anywhere employment has created vastly greater security risks....

Oracle Autonomous Database for Dummies
What if your database could install, manage, secure, and upgrade itself—with little or no manual administration...

Ransomware Protection with Pure Storage® and Commvault
Ransomware attacks continue to be top of mind for business and IT leaders. And for good reason. They...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.