Disaster Recovery
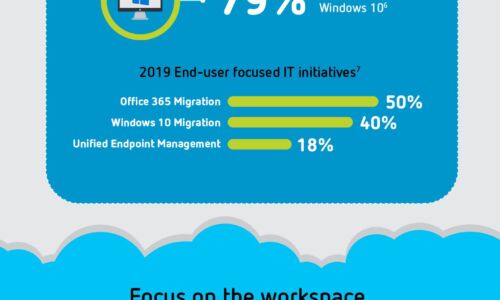
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...

Seven Strategies to Securely Enable Remote Workers
Is your organisation ready to securely support a wide range of remote workers in the wake of a global...

Shift your Web Security to the Cloud, for the Cloud
As enterprises embrace digital transformation, the adoption of software-as-a-service (SaaS) is robust...

CompTIA A+ Certification All-in-One For Dummies, 5th Edition
Fully updated to cover the 2019 exam release! CompTIA's A+ certification is an essential certification...

Which WAF is right for me eBook
Despite the tech industry's collective best efforts to bolster secure application development practices,...

Ransomware Protection with Pure and Veritas
Ransomware attacks continue to be top-of-mind for business and IT leaders. And for good reason. Ransomware...

The Best of Both Worlds: Hybrid IAM Offers Flexibility and Enhanced Security
One of the fastest growing segments of the Identity and Access Management (IAM) market is the cloud segment. Increasingly,...

The Total Economic Impact™ Of Dell EMC Servers For SAP
To run a digital business that is Intelligent and agile, your enterprise requires an IT landscape capable...

Kubernetes on vSphere For Dummies
Discover how building and running containerized applications with Kubernetes on vSphere drives business...

How 3 Leading Companies Found Peace of Mind with Disaster Recovery
Many traditional DR solutions are unreliable, complex and expensive, requiring significant and time-consuming...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


