Digital transformation

Migration 8 Best Practices
Deliver cloud value faster with 8 Best Practices to Make Your Cloud Migration a Success. Thousands of...

Building the Business Case for ITAM
IT Asset Management (ITAM) is a set of business practices that enables organizations to better manage...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...
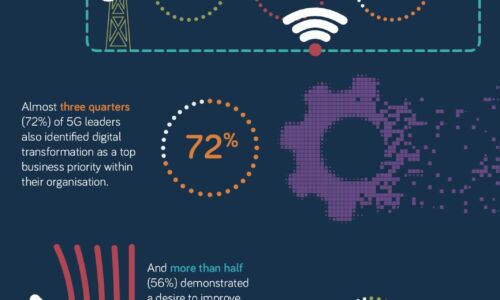
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

The Only Certainty is Uncertainty
We cannot anticipate change, although we can bet on its coming, be it from weather, pandemics, socio-political...

The Book of Knowledge - HAandLC
Gartner predicts that 65% of all app development activity will take place on low-code platforms by 2024....

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...

Encryption Is Now a Trojan Horse: Ignore It at Your Peril
The game of leapfrog between hackers and data security professionals continues. No sooner do organizations...

Microsoft Teams & Telephony
Leveraging calling services from a UCaaS provider, integrated with Microsoft Teams, provides organizations...

All-Flash Buyer's Guide: Tips for Evaluating Solid-State Arrays
Think Flash-First for Primary Storage. The introduction of enterprise-grade all-flash arrays has turned...

Unified Endpoint Management (UEM): Address 3 Common Challenges
With digital transformation comes mobile devices, apps and high-speed connectivity that make it possible...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


