Cloud Computing

Harden Your Defenses With Security Analytics
Analyze data in real time with the right SIEM approach. It's time to step up your security game. If you...

The Guide to Building a Winning Data Strategy
This MIT Sloan Management Review Executive Guide covers why culture is the greatest barrier to success,...
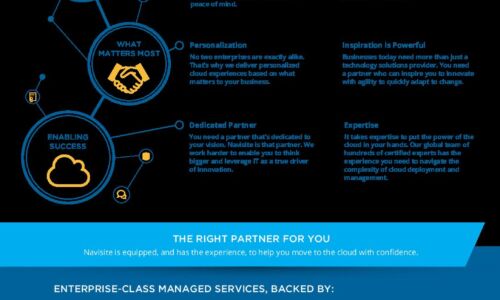
Move to the Cloud with Confidence
Navisite is a leading international provider of enterprise-class managed cloud services. But our story...

Upgrade to State-of-the-Art Log Management
Most log messages traditionally come from three types: system logs of servers, network devices, and applications....

How to Accelerate Container Adoption
Developing applications with containers has become an increasingly popular way to operationalise speed,...

The Future Is Flexible: Six Areas to Make It Work.
Over 50% of businesses are preparing for long-term, flexible work patterns. But the rush to adopt remote...

How To Stop Lateral Attacks With Workload Microsegmentation
Network segmentation is a widely accepted tool for improving performance and boosting security. By splitting...

7 Critical Reasons for Office 365 Backup
You have one more reason added to the 6 critical reasons to protect your Office 365 data. This 5-minute...

Use Case - Optimizing SIEM
Security Information and Event Management (SIEM) solutions form the core of many organizations' security...

6 Misconceptions about Collective Defense for Cybersecurity
Collective Defense uses collaboration and threat information sharing in new and powerful ways to reduce...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



