Virtualization

Sharing the Workload of Workload Security
Security teams need the help of IT operations to secure workloads IT admins and security teams both play...

Protect and Preserve Your Data from Endpoint to Infrastructure
Technology has made it possible for the world to maintain a somewhat business-as-usual stance, even when...

Migrating Apps to the Cloud in 5 Steps
Cloud applications, platforms and services are changing the way enterprises compete for customers. The...
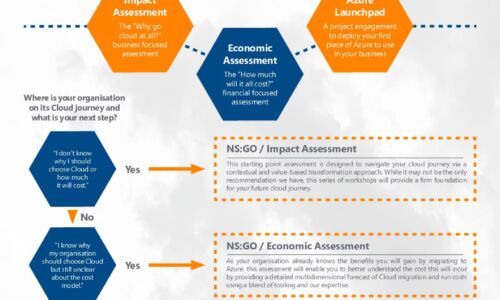
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Why digital transformation is the only option for businesses today
Over the last ten years, digital transformation has changed the landscape of global business. In this...

Securing financial services network data
Financial services is one of the most tightly regulated business sectors. The FSA, the Data Protection...

Complete Protection at the Edge Whitepaper
How effective protection at the edge can secure the most critical assets, mitigating threats closest...

VP AppDev Confessions
Development teams burdened with complex release requirements often run over schedule and over budget....

The Top 10 Reasons to Upgrade to VMware vSphere 7
Customers today demand rapid delivery of innovative applications. To meet those demands, businesses must...

Next-Generation Anti-Malware Testing For Dummies
How did you choose your anti-malware solution? Did you put it through the same rigorous process as your...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



