Server

5 Critical Considerations for DDoS Mitigation
Distributed denial-of-service (DDoS) attacks remain one of the most effective methods used by cybercriminals...

Futureproofing IoT
Greater connectivity will bring huge opportunities, but companies and the public must be wary of threats...

Economic Impact: Veeam Cloud Data Management
TEI Report: Reduce operating costs of data backup and recovery while reducing data-related risk. ...

Building Your MSP Security Offerings
As a managed service provider (MSP), your customers already expect you to keep their networks secure....

Database Solutions Pocket Book
Given the fast pace of modern business, traditional enterprise infrastructure is ill-suited to meet the...

Inside The Mind of a Hacker 2019
The first step in cybersecurity? Think like a hacker. According to a recent report, 71% of cybercriminals...

The Top 10 Reasons to Upgrade to VMware vSphere 7
Customers today demand rapid delivery of innovative applications. To meet those demands, businesses must...

Ransomware Prevention and Remediation
The global damage costs of ransomware are projected to reach $20 billion in 2021. This includes not only...

Threats to DNS Are Threats to Your Business. What You Can Do
DNS is a foundational part of the internet, and its hierarchal structure is well known and understood....
Don’t Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

The Top Five Reasons to Choose Toad Over SQL Developer
Now that DevOps initiatives are becoming the norm, you're under increasing pressure to deploy application...
How to Protect Your Organisation from Identity-Based Attacks
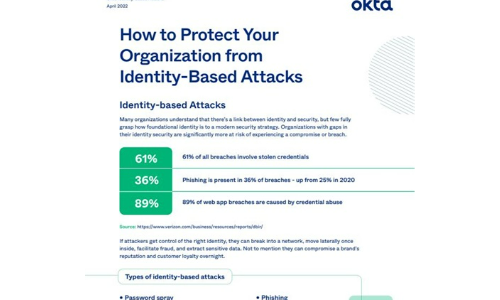
Many organizations understand that there's a link between identity and security, but few fully grasp...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

