Security Management

Ransomware Prevention and Remediation
The global damage costs of ransomware are projected to reach $20 billion in 2021. This includes not only...
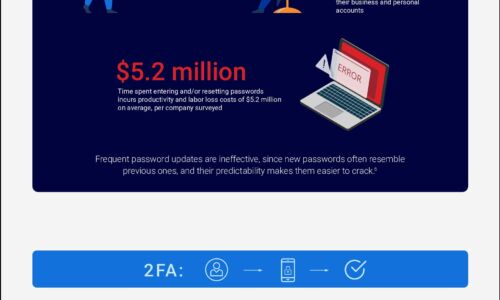
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

A Guide to Assessing Security Maturity
Cybersecurity is an unavoidable part of daily business operations for organizations of all sizes and...

Reduce Cloud & Container Complexity, Improve Cost Efficiencies
Visibility into ever-growing containerized environments, better application context for alerts, faster...

The US Customer Experience Decision-Makers' Guide 2019-20
The US Customer Experience Decision-Makers' Guide is a major annual report studying the CX strategy,...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...

Critical Event Management
For today's organizations, the threat of disruptions that critically impact people and business is unavoidable....

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

Enhanced Privilege Access Management Solutions
Privileged Access Management (PAM) is one of the most important areas of risk management and security...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

