Network

Architecting the Zero Trust Enterprise
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit...

Cloud Security Automation For Dummies®
Get the big picture on cloud security, in all its complexity, speed, and scale. Our Cloud Security Automation...

Deliver agility with an expanded vision for SandOP
Though sales and operations planning (SandOP) originally aspired to bring business functions together...

MSP Security Best Practices: Ransomware Attack Prevention
In Datto's Global State of the Channel Ransomware Report, 4 in 5 managed service providers (MSPs) agreed...

IPv6 migration with Micetro by Men&Mice
IPv6 adoption has been slow in the corporate world. Despite global IPv6 traffic increasing with 500%...

Migrating to the Public Cloud: Three Success Stories
Organizations find the public cloud appealing for its promises of agility, reduced costs and developer-friendly...

7 Experts on Optimizing Your Security
Security teams have a difficult task to perform, and it's not getting any easier. IT environments are...

Ransomware Case Studies
Ransomware is a simple name for a complex collection of security threats. Attacks can be short and brutal,...
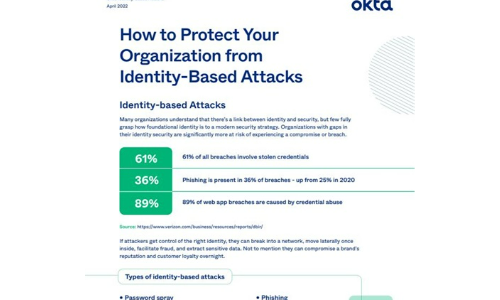
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Migrate, modernize, transform
To win in the digital era, companies are seeking new ways to build apps and services, connect previously...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



