Network Monitoring

7 Key Considerations for Microservices-Based Application Delivery
As you modernize your applications with microservices-based architecture and Kubernetes, you must also...

10 Hidden Costs of an On-Premises Phone System (PBX)
Many on-premise phone system (PBX) manufacturers claim that the five-year costs of their systems are...

5 Ways that SD-WAN Transforms your Network
SD-WAN transforms your network by making it more responsive, providing greater bandwidth and being more...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...

Python for Data Science For Dummies, 2nd Edition
The fast and easy way to learn Python programming and statistics Python For Data Science For Dummies...

How to Help Prevent Increasingly Rampant Brand Exploitation
Brands have been the unwitting victims of scams since time immemorial. Now, in the age of phishing, it's...

Unified Promotions: An Offer Hard to Resist
Promotions are no longer a bait to lure customers and clear excess stock, they are now part of retailers'...

The Essential Guide to Preparing Your Network for the Cloud
How to meet your network requirements at every stop of your cloud transformation. In this eBook, we'll...

Go Mainstream with SD-WAN: Migration Best Practices
Over the last couple of years, SD-WAN technology has matured into a mainstream solution. Yet, the most...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...

Aruba Unified Infrastructure
Network infrastructure and operations teams have never been more stretched. Hyper-distributed edge environments...
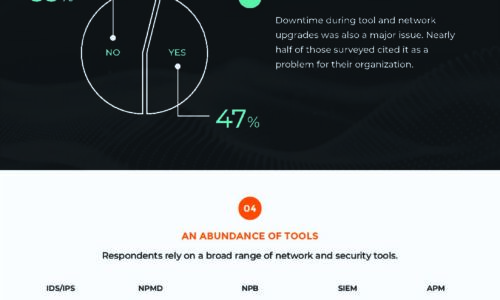
7 Insights into Today’s Network Monitoring and Management Approaches
Managing today's complex networks isn't an easy task to navigate. Network operations teams must contend...
- 1
- 2
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

