Hardware

The Impact of Moving to Independent, Third-Party Software Support
When organizations consider the amount of their IT budget that is spent on yearly maintenance, many focus...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...

Selenium Grid Build vs. Buy
Automated testing is essential to software development teams that are moving to continuous integration...

Unified Endpoint Management (UEM): Address 3 Common Challenges
With digital transformation comes mobile devices, apps and high-speed connectivity that make it possible...

Take the fight to the cybercriminals
An IT leader's guide to keeping your business running with proactive cybersecurity. It's an incredibly...

DDoS attack trends for Q2 2021
Cloudflare's network protects approximately 25 million Internet properties, giving us deep insight into...
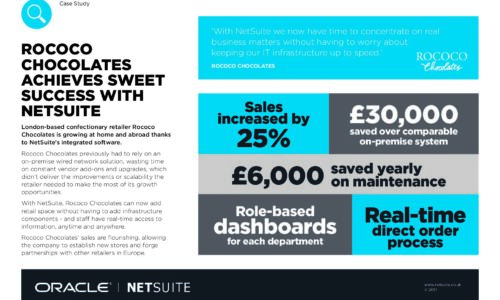
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

Securing Endpoints Amid New Threats
Giving employees the flexibility to be fully productive while working remotely makes it critical that...

2021 State of the Intelligent Information Management Industry
2021 is shaping up as a year of opportunity for many organizations in building out their information...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...

The Beginner's Guide to Dynamic Case Management
What is dynamic case management? Who is using it and how can it help you prepare for the future of work? The...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


