Endpoint Security

2 Steps to Achieve Endpoint Compliance with KACE® by Quest
Next to ongoing security issues, meeting compliance mandates is one of the biggest challenges IT professionals...

The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...
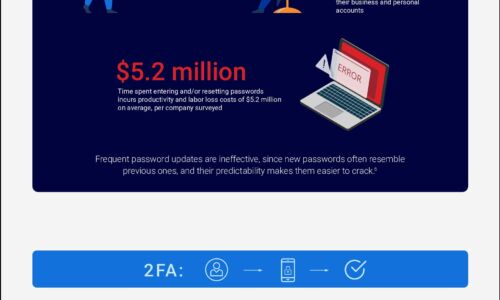
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


