Embedded Systems

Windows 10 for Dummies, 2nd Edition (Full eBook)
The most comprehensive guide to Windows 10, updated with the latest enhancements. This eBook includes...

The Survivor's Guide to Building an Office 365 Network
A Microsoft Office 365 deployment can be daunting. From a fast user experience, to a cost-cutting productivity...

Prevent Ransomware From Cyber Disaster
Modern ransomware is one of the most significant cybersecurity threats to critical services, compute...

The IT Salary and Skills Report 2017 (100 Page Full eBook)
What does your industry look like? Download this comprehensive IT industry salary report, with data from...

Improve Productivity with Box and Office 365
In this guide, discover why Box is the perfect complement to Office 365 — and all the other apps you...

Conversational Teams Management and Migration
The abrupt transition to everyone working from home forced IT to cut through all of the usual bureaucracy...

CompTIA A+ Certification All-in-One For Dummies, 5th Edition
Fully updated to cover the 2019 exam release! CompTIA's A+ certification is an essential certification...

IT and Cyber Incident Response Communication Templates
BlackBerry® Alert is a critical event management (CEM) solution designed to help organizations prepare...

Take Control of your Office 365 Data
This short, easy-to-read analyst report by 451 Research provides their view on the importance of backing...

Managing Critical Events with BlackBerry Alert
Every day, organizations face risks from natural, technological, and human-caused critical events. While...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...
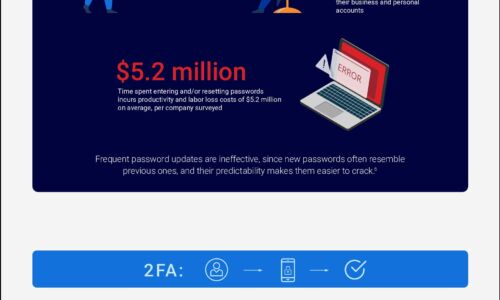
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

