Compliance

Low-Code Guide
Low-Code development is the way to build apps more quickly by reducing the need to code. But that's not...

Security Operations Use Case Guide
Responding to security incidents and vulnerabilities is an ongoing process, and you know that reacting...

Managing Sprawl in Microsoft 365
How content sprawl happens, why it matters, and steps every IT leader should take to avoid it. Sprawl...

High Speed Network Encryption
High Speed Encryption (HSE) secures data in transit and data in motion, as it moves across the network...

Secure Digital Transformation Requires Identity-Based Access Control
Digital transformation is an all-encompassing term that refers to a wide swath of activities designed...
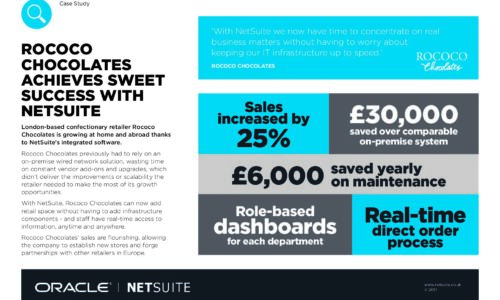
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

A Five-Step Plan to Move Your Apps to the Cloud
Cloud applications, platforms, and services are changing the way enterprises compete for customers. The...

Enterprise Cloud Solutions
Many traditional infrastructure vendors would have you believe that hyperconverged infrastructure is...

CISO’s Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

Security and Legal: An Essential Collaboration
Legal and security departments share the common goal of protecting an organisation from harm. But, while...

Delivering Business Transformation for Fintech Companies
The financial sector has seen an influx of innovation and competition in recent years led by fintech...

Redefining Modern Master Data Management in the Cloud
Your organization needs to continuously innovate to stay competitive. And business insights are necessary...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

