BYOD

The Forrester Wave™: Big Data NoSQL
In this report, Forrester states that, 'NoSQL has become critical for all businesses to support modern...

Migrating Apps to the Cloud in 5 Steps
Cloud applications, platforms and services are changing the way enterprises compete for customers. The...

Cloud Security Report 2022
Cloud adoption continues to permeate throughout organizations as they embrace agile software development....
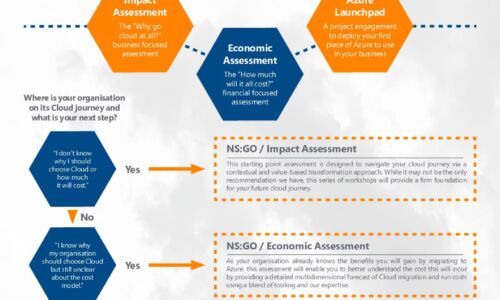
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Sauce Visual Component Testing
Sauce Visual Component Testing provides organizations the ability to quickly automate the testing of...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

Back to the Basics: Cyber Hygiene Starts with Asset Management
The challenge: managing millions of dynamic, distributed and diverse assets while maintaining high standards...

Spotlight: The State of the UK and Ireland Mid-Sized Business and IT
Medium-sized businesses are central to our economies, but this varied market is hard to analyse. So,...

Modernize the customer experience with your apps
Delighting customers starts with the right cloud foundation, Understanding the multi-cloud world is critical...

Modern infrastructure for better end user experiences
Many companies with existing EUC deployments are refreshing their technology stacks to deliver a better...

Fleet ELD mandate
With the ELD mandate in effect, companies with vehicles requiring fleets that use paper logs to track...

Ponemon Cost of Insider Threats Global Report
Independently conducted by Ponemon Institute External attackers aren't the only threats modern organisations...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

